TOKEN SECURITY SCHEME
Hello Everyone…
This is good news for all investors and everyone, I will introduce a good project for your future. Because I am very happy with this project, they created it for us all. I really hope that the articles and information I share with you will benefit all those who see and read them and those who have participated in this project. Hope you are lucky.
Well now I will explain to you all.
Attacks on exchange places and platform/repository for coins and
Key storage has resulted in huge losses as it is
indicated by the MtGox event, and with increasing list of places
exchanges that were closed due to the massive thefts and
joined the famous “Blockchain Graveyard” list. Character
These attacks vary, and may involve direct attack, attack
DDoS, phishing from stakeholders, data theft, etc. With
So, there is an immediate and urgent need to know
how the digital keys are secured and properly managed and
how all blockchain technologies can be stored and protected on a regular basis so that it can fully minimize the theft of cryptocurrency assets and other digital assets, be it a private holder, shared savings, or anything else.
Our cyber security experts are experienced and knowledgeable
depth about Payment and Banking Industry (PBI or the payment
and banking industry ry’s), digital key management has revealed
important findings that can be applied to the crypto currency ecosystem.
We note that major global institutions have implemented Modules
Hardware Security (HSMs or Hardware Securit y Modules) for several decades to protect user assets and customer assets them with success. In the crypto currency ecosystems decentralized, proposed distribution of HSM (DHSMs or Dist fuss ed ed HSM) in the revolutionary Token Security Scheme (TSS) and enhanced features and applications, aims to address the existing security gaps well for the crypto currency ecosystem with the aim of capturing attacks (either simple, complex, professional or otherwise) at the place of exchange or facility which stores the digital assets.
Key storage has resulted in huge losses as it is
indicated by the MtGox event, and with increasing list of places
exchanges that were closed due to the massive thefts and
joined the famous “Blockchain Graveyard” list. Character
These attacks vary, and may involve direct attack, attack
DDoS, phishing from stakeholders, data theft, etc. With
So, there is an immediate and urgent need to know
how the digital keys are secured and properly managed and
how all blockchain technologies can be stored and protected on a regular basis so that it can fully minimize the theft of cryptocurrency assets and other digital assets, be it a private holder, shared savings, or anything else.
Our cyber security experts are experienced and knowledgeable
depth about Payment and Banking Industry (PBI or the payment
and banking industry ry’s), digital key management has revealed
important findings that can be applied to the crypto currency ecosystem.
We note that major global institutions have implemented Modules
Hardware Security (HSMs or Hardware Securit y Modules) for several decades to protect user assets and customer assets them with success. In the crypto currency ecosystems decentralized, proposed distribution of HSM (DHSMs or Dist fuss ed ed HSM) in the revolutionary Token Security Scheme (TSS) and enhanced features and applications, aims to address the existing security gaps well for the crypto currency ecosystem with the aim of capturing attacks (either simple, complex, professional or otherwise) at the place of exchange or facility which stores the digital assets.
SOLUTION
Many security-conscious institutions rely on HSMs for protect and manage their digital keys and protect such assets ATM machines, mainframe access and operations, point-of-sale machines (POS) as well as for verify and sign a SWIFT message. Basically, they are used in almost any application that requires a digital signature that is safe and verified. For example, HSM in bank data centers, used to validate your PIN when you withdraw money from an ATM, or validate cryptogram transactions when you buy goods in POS terminals traders. In this case, only HSM is under the control of the bank which has access to the correct key to perform that processing secure.
HSMs has anti-interference technology to clear confidential information in the event of one or more physical offenses. Their architecture is designed
with secure crypto processor chip and various physical security measures
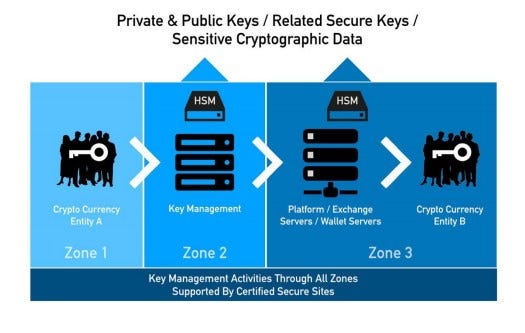
active to effectively reduce and mitigate the source channel side attack or probing bus. This device is widely used in banking, government and institutions where important confidential information should be protected and have succeeded in their role to reduce and prevent successful hacking. A current analogy information, key management activities and HSM applications are illustrated on Picture.
with secure crypto processor chip and various physical security measures
active to effectively reduce and mitigate the source channel side attack or probing bus. This device is widely used in banking, government and institutions where important confidential information should be protected and have succeeded in their role to reduce and prevent successful hacking. A current analogy information, key management activities and HSM applications are illustrated on Picture.
To improve security features and minimize the possibility of attack
which succeeds against the crypto currency ecosystem, the cyber expert team advocates new projects and standards (called Token Security Scheme [TSS])
to present the best practices of the Payment Card Industry, which will
improved further and called the EPCI Standard. Our proposal allows flexibility for customers and stakeholders to have the key privately managed person with HSMs placed in in our partner network for PCI certified facilities. Each of these facilities acts ‘always on standby’ for anything and everything else in times of crisis as a means of business contingency management for our customers. These DHSMs, coupled with our proposed architecture, make it highly unlikely for any hacker to successfully extract the master seeds they want.
which succeeds against the crypto currency ecosystem, the cyber expert team advocates new projects and standards (called Token Security Scheme [TSS])
to present the best practices of the Payment Card Industry, which will
improved further and called the EPCI Standard. Our proposal allows flexibility for customers and stakeholders to have the key privately managed person with HSMs placed in in our partner network for PCI certified facilities. Each of these facilities acts ‘always on standby’ for anything and everything else in times of crisis as a means of business contingency management for our customers. These DHSMs, coupled with our proposed architecture, make it highly unlikely for any hacker to successfully extract the master seeds they want.
For cryptocurrency, private key is an important asset in which people are
having access to the key must also have full control over the asset.
Thus, the security of personal keys and management is very important.
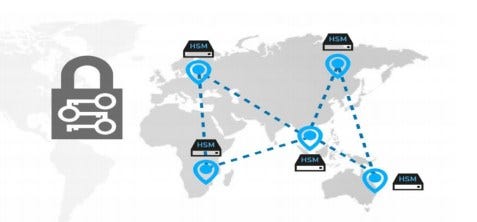
Figure 3 shows how the key in crypto currency transactions
generally transmitted, encrypted, processed and managed.
having access to the key must also have full control over the asset.
Thus, the security of personal keys and management is very important.
Figure 3 shows how the key in crypto currency transactions
generally transmitted, encrypted, processed and managed.
Their team review of various exchanges found that at present,
most crypto currency exchanges and their related entities do not
has a standard and effective key management system that is equivalent to
PCI compliance standards. Most of them are based on ad systems
hoc that is open to being attacked by malicious hackers. They are also based
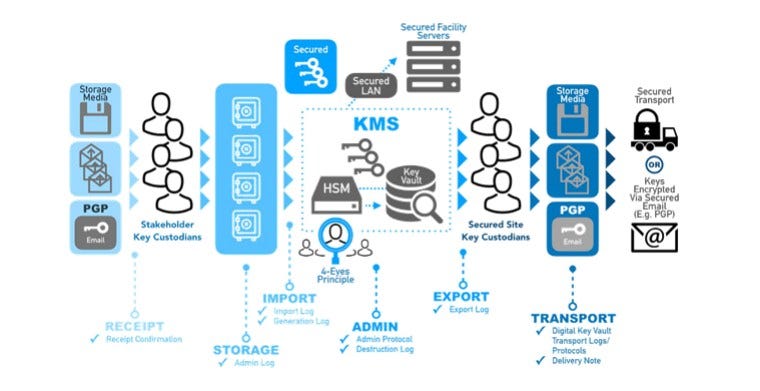
software and not hardware based systems with HSM special (which is the practice and standard of PCI in general). Incident as the appropriation of Mt Gox highlights the dangers of implementing the system such ad-hoc security and we advocate that security feature refined from the Key Currency Management System of cryptocurrency (CKMS) to eliminate recurrence of similar events. Picture 4 shows various key management modules in the crypto currency ecosystem.
most crypto currency exchanges and their related entities do not
has a standard and effective key management system that is equivalent to
PCI compliance standards. Most of them are based on ad systems
hoc that is open to being attacked by malicious hackers. They are also based
software and not hardware based systems with HSM special (which is the practice and standard of PCI in general). Incident as the appropriation of Mt Gox highlights the dangers of implementing the system such ad-hoc security and we advocate that security feature refined from the Key Currency Management System of cryptocurrency (CKMS) to eliminate recurrence of similar events. Picture 4 shows various key management modules in the crypto currency ecosystem.
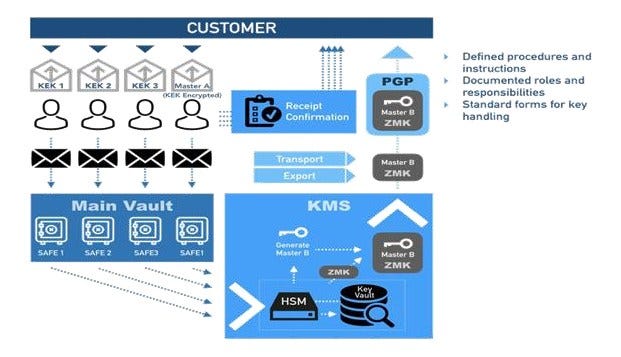
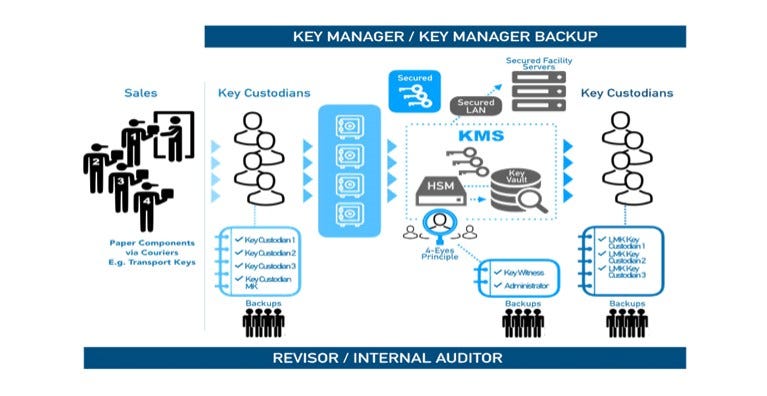
In CKMS, we will develop and implement a combination version Secret Key and Public Key to qualify symmetric cryptography for fast processing and asymmetric cryptography for large networks The advantages of CKMS that we offer are further enhanced with the audit regular conducted by the EPCI certified auditor to ensure full compliance with EPCI standards at any time. This needs to be done avoid human mistakes and make sure even the technology Other best security is carefully audited in its internal processes. The audit process is illustrated in Picture 5.
Patent Design Protection
The security features we propose, refinement and distributed architecture is in the process of being drafted and filed for patent protection. It is our intention to finally grant this patent license to the parties thirds who wish to apply this invention to the solution/structure/process or for further development of the security platform or for bind financial institutions with a view to developing implementation in the future in FINTECH’s view.
Our TSS solution allows client cryptocurrency to be secured at in our DHSMs network that are within EPCI certified facilities at all over the world, thus ensuring the security and legacy of wealth for future generations. This will ensure that not only we can safely developing and integrating the cryptocurrency using the traditional financial and card payment industry, but also helping to set newly refined standards for ecosystems future cryptocurrency.
Our TSS solution allows client cryptocurrency to be secured at in our DHSMs network that are within EPCI certified facilities at all over the world, thus ensuring the security and legacy of wealth for future generations. This will ensure that not only we can safely developing and integrating the cryptocurrency using the traditional financial and card payment industry, but also helping to set newly refined standards for ecosystems future cryptocurrency.
Some of the advantages DHSM they offer include:
- Saved keys are guaranteed within the DHSM limit: the key is always in live in the safe, EPCI certified and DHSM boundary.
- Hardware Tamper-resistant: FIPS 140–2 Level 2 and 3 certified DHSMs are tested with stringent standards.
- Sophisticated cryptography: DHSMs uses certified, cryptographically safe cryptographic random generators, to generate keys to provide superior quality keys.
Institutional and Ultra High Net-worth Individuals (UHNWI), holding millions the crypto currency will be confident that their assets will not be stolen easily, simply because (a) their private key is generated by and maintained safely in high security wallets and not on platforms vulnerable to the software wallet, and (b) this physical wallet is guaranteed with EPCI standard facilities; and © all security processes are strictly applied and subject to regular professional audits.
Cases of Future Use
The DHSMs TSS Network we propose in EPCI certified facilities with a thorough CKMS procedure will provide a powerful, place solution which is safe for long-term storage with a given digital asset equal treatment and security as many words of that asset in fact. This level of security encourages a number of use cases
to be developed in many industries (including the traditional financial industry) to utilize Blockchain technology.
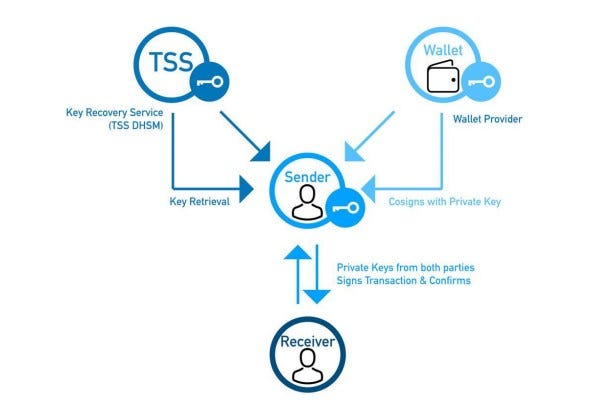
Their partner networks, including Mr.Uwe Martin Wittig, will work together
with us to develop additional safety and security features for authentication and identity verification to provide a safer and more convenient way to perform online financial activities with greater privacy. We intend to further develop better security applications and integrate them with crypto currency purses, payment cards, crypto currency exchange for more security. Finally, as a premium, we will create SecureCrypt oVault for fund management industries, family offices and UHNWI. Our solution can also be used for the management of the actual wallet key and for key recovery purposes as shown in Picture 6.
to be developed in many industries (including the traditional financial industry) to utilize Blockchain technology.
Their partner networks, including Mr.Uwe Martin Wittig, will work together
with us to develop additional safety and security features for authentication and identity verification to provide a safer and more convenient way to perform online financial activities with greater privacy. We intend to further develop better security applications and integrate them with crypto currency purses, payment cards, crypto currency exchange for more security. Finally, as a premium, we will create SecureCrypt oVault for fund management industries, family offices and UHNWI. Our solution can also be used for the management of the actual wallet key and for key recovery purposes as shown in Picture 6.
Their main objective is to integrate the proposed TSS, DHSM, EPCI, CKMS and SecureCryptoVault with physical wallets and payment cards which will be built with secure redundancy features and advanced features others with different categories of user privileges. With a safer environment made possible by the TSS we offer (which will be implemented systematically and holistically) within the ecosystem Blockchain, in turn, opens the door to other usage cases which is limited only by their imagination.
Roadmap
That’s my explanation of the TOKEN SECURITY SCHEME project, a good project for us and a cryptocurrency lover. They strengthen the security of our wallets from hacking theft. Welcome to join the TSS project
More information about TOKEN SECURITY SCHEME please visit the website and other contact information below:
ANN THREAD | WEBSITE | FACEBOOK | TWITTER | YOUTUBE | TELEGRAM
Author:
My Bitcointalk Profile Link: https://bitcointalk.org/index.php?action=profile;u=1229230
My ETH Wallet ;0x29AF24D027E5A0A74427A2A4D5dDFe09803D5F93
Tidak ada komentar:
Posting Komentar